Introduction
This page is dedicated to the cryptographic hash function family called RadioGatún, which we presented at the Second Cryptographic Hash Workshop, Santa Barbara, August 24-25, 2006.
The design of RadioGatún improves upon the one underlying the Panama hash function. The majority of other hash functions is based on the Merkle-Damgård construction, which relies on a collision-resistant fixed-length compression function. Instead, our design focuses on a variable-length compression function, based on the iterated application of a single round function on a state; this is the alternating-input construction. Furthermore, the state of RadioGatún is divided into two parts, one called the belt and the other the mill. We say that it follows the belt-and-mill structure.
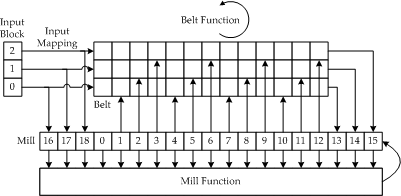
The structure of RadioGatún (larger)
The operations used in this hash function are bitwise logical operations such as AND, XOR, NOT and cyclic shifts on words. Actually, the size of words that RadioGatún processes can take any value between 1 and 64, hence composing a family of hash functions. Among the family, RadioGatún[64], with 64-bit words, is the default choice and is optimal for 64-bit platforms. For best performances on 32-bit platforms, RadioGatún[32], with 32-bit words, can also be used. Note that the security claims depend on the chosen word size, as specified in the paper.
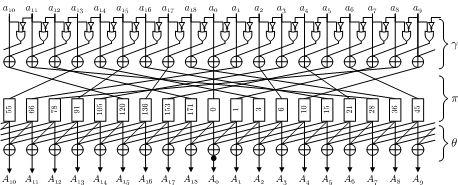
The logical operations applied to the mill (larger)
One of the advantages of RadioGatún is its good performance. In software, RadioGatún is quite competitive with SHA-1. Also, RadioGatún is compact and extremely fast in hardware.
More information can be found in the files available on the right pane.
RadioGatún is not a sponge function

Note that RadioGatún does not make use of the sponge construction [1] and so cannot be called a sponge function.
Specifically, the differences between RadioGatún and the sponge construction are the following:
- In the sponge construction the input is applied to and the output is extracted from the same part of the state. This is in fact essential for the simplicity of the indifferentiability proof of the sponge construction. In RadioGatún this is not the case.
- In RadioGatún there are a number of blank rounds between the application of the input and the extraction of the output. There are no blank rounds in a sponge function.
Furthermore, RadioGatún predates the sponge construction. In the RadioGatún paper the security claim was expressed with respect to something called an ideal mangling function, which is different from a sponge function. The security claim is now expressed as a flat sponge claim (see below), but this does not imply that the function has to follow the sponge construction.
Disclaimer
The RadioGatún hash function is a work in progress and serves research purposes. It should not be used or implemented for other purposes than research.
Errata
A list of corrections (version 2007-03-09) is available in PDF format.
Security claim
In the original RadioGatún paper, we formulated the claim using a so-called ideal mangling function. This was an early attempt at what we now call a random sponge. We now prefer to express the security claim for RadioGatún as a flat sponge claim [1] with capacity 19w, with w the word length (e.g., for RadioGatún[64], a capacity of 1216 bits).
Basically, this comes down to saying that (truncated) RadioGatún[w] is as strong as a (truncated) random oracle with respect to any attack, where the success probability of the attack is lower bounded by N2/219w, N being the computational effort of the attack expressed in terms of number of calls to the round function (or in other words, as long as the effort of the attack is upper bounded by 219w/2 calls to the round function).
Reference
[1] G. Bertoni, J. Daemen, M. Peeters and G. Van Assche, Sponge Functions, Ecrypt Hash Workshop 2007.
Contact Information
Email: radiogatun -at- noekeon -dot- org